Phishing has become one of the most common and dangerous forms of cyberattacks in the digital world. Every day, attackers send millions of fake emails, text messages, and links designed to trick people into revealing sensitive information. Whether you are an individual, a business owner, or a developer, understanding phishing is key to staying safe online. In this article, you will learn how phishing attacks work, how to identify them, and what steps you can take to protect yourself.
Understanding Phishing Attacks and How They Work
Phishing is a type of cyberattack where criminals impersonate trusted entities—such as banks, employers, or popular websites—to deceive a user into sharing private details. These details often include passwords, credit card numbers, or personal identification information. Attackers rely on psychological manipulation, making their messages appear urgent or tempting to provoke quick responses.
Most phishing campaigns start with an email or message containing a malicious link or attachment. When the user clicks on it, they are directed to a fake website that looks legitimate. This site then collects the user’s credentials or installs malware on their device. Because phishing messages mimic real communication so closely, it can be difficult to distinguish between what’s real and what’s fake.
Interestingly, phishing attacks have evolved over time. Modern attackers use sophisticated tools powered by artificial intelligence to craft highly personalized messages. This technique, known as spear phishing, targets specific individuals or companies using information gathered from social media and other public sources. The more realistic the message, the more likely it is to be successful.
Understanding the mechanics behind phishing helps users recognize that the threat is not just technical—it’s psychological. Cybercriminals exploit human emotions like curiosity, fear, and greed. By identifying how attackers think and operate, you can better recognize suspicious digital interactions before they cause harm.
Common Signs to Identify a Phishing Attempt
Recognizing a phishing attempt can save you from serious data loss or financial damage. One of the most obvious indicators is an unexpected email or message asking for personal or financial information. Legitimate organizations rarely request sensitive details through email or instant messaging. Additionally, phishing messages often contain spelling errors, poor grammar, or slightly misspelled domain names that give them away.
Another common sign is a sense of urgency or fear within the message. For example, you might receive an email claiming your account is suspended or compromised unless you act immediately. These are tricks designed to rush you into clicking a malicious link or downloading a dangerous attachment without thinking. Always take a moment to verify the message before responding.
Fake links are another hallmark of phishing attempts. Even if the text looks like a legitimate website, hovering over the hyperlink often reveals a suspicious or unfamiliar URL. Similarly, attachments from unknown senders can contain malware that infects your device as soon as you open them. It is always safer to delete messages that look questionable instead of investigating them through risky clicks.
Lastly, phishing messages might use logos and branding from real companies to appear trustworthy. For added safety, check such emails by visiting the official website directly or contacting the organization’s customer support through official channels. Remember, when in doubt, avoid engaging with the message at all.
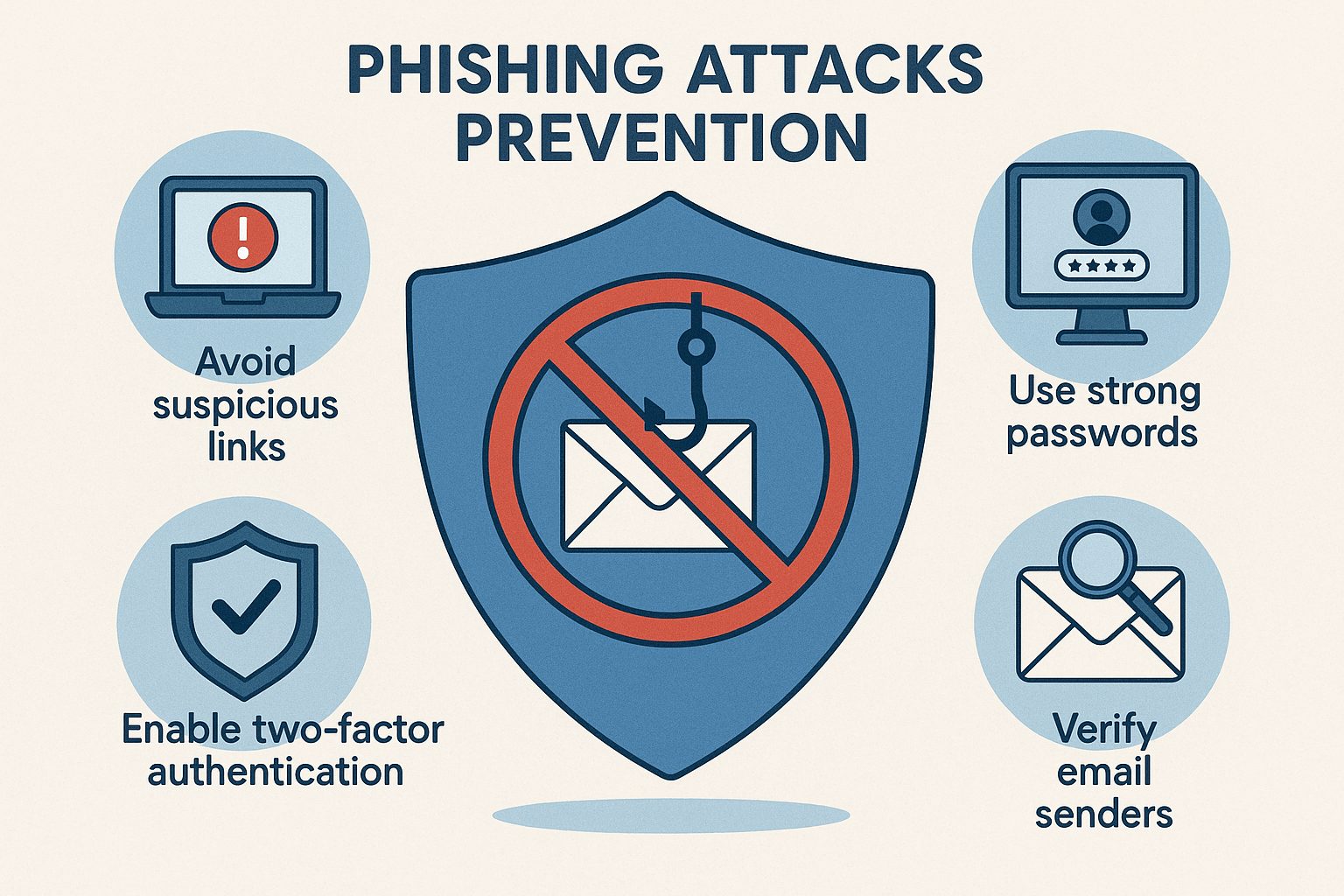
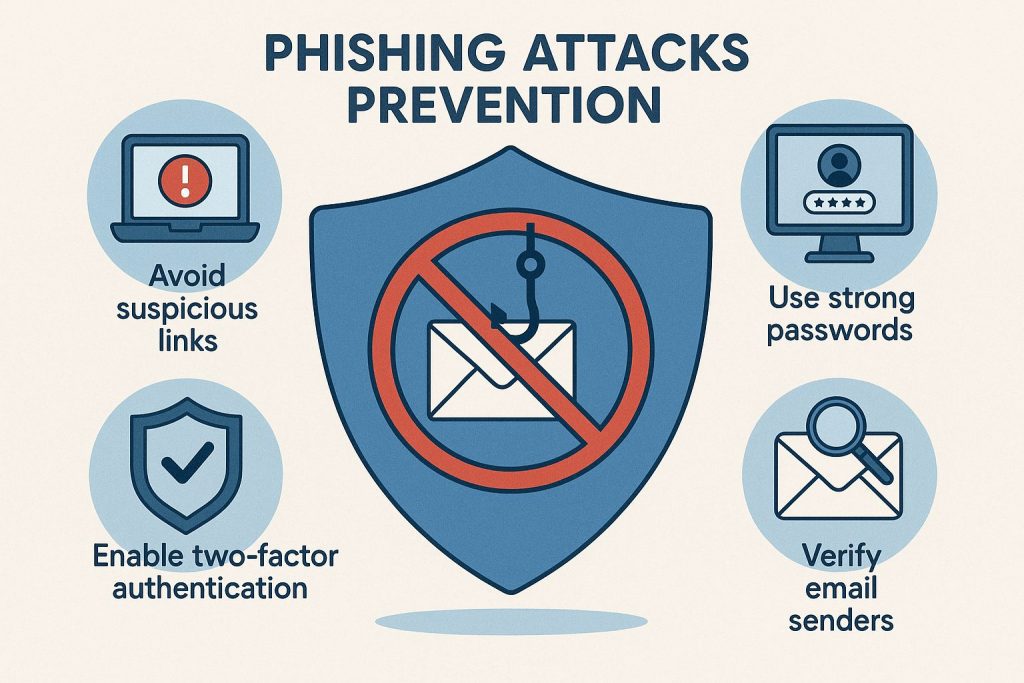
Best Practices to Protect Yourself from Phishing
Preventing phishing requires combining awareness with technical knowledge. Start by using email filters and enabling spam detection in your inbox to block suspicious messages automatically. Keeping your operating system, browsers, and security software updated also reduces vulnerabilities that attackers can exploit. Regular updates often include patches for known security loopholes that phishing campaigns rely on.
Another useful defense is multi-factor authentication (MFA). Even if a criminal steals your password, MFA adds an extra layer of protection by requiring another step—like a text code or authentication app approval—before accessing your account. It’s one of the most effective ways to defend against unauthorized access.
Education is also vital. Take time to educate yourself, your employees, or your family members about how phishing works. Run awareness programs and simulated phishing exercises to test knowledge and preparedness. The more people know about identifying phishing attempts, the smaller the risk of falling victim to them.
Lastly, use secure password management practices. Create strong, unique passwords for every account and store them in a reliable password manager rather than reusing them. This greatly limits the damage in case one of your accounts is compromised. Phishing prevention is not a one-time measure—it’s an ongoing process of vigilance and smart habits.
What to Do If You Fall Victim to a Phishing Scam
Even the most tech-savvy individuals can fall for phishing attacks. If you suspect you’ve shared sensitive information with a fake site or have downloaded a malicious file, act immediately. Change your passwords for the affected accounts and any related services. If the same password was reused elsewhere, change it across all accounts.
Next, notify the company or service that was impersonated. Many businesses have dedicated fraud teams that can help secure your account or investigate the incident. It’s also important to report phishing attempts to national cybersecurity agencies or relevant authorities. Reporting helps track and block future phishing campaigns.
Monitor your bank and credit card statements for unusual transactions. If financial information was compromised, contact your bank immediately to freeze or monitor your account. In some cases, you may need to request a credit freeze or enable alerts to protect yourself from identity theft.
Lastly, run a malware and antivirus scan on your device to ensure no malicious programs were installed. Learning from the experience is key—use it to strengthen your awareness and reinforce protective measures. Cybersecurity is a continuous learning journey, and even mistakes can help you build resilience.
Phishing remains one of the most effective tools in a cybercriminal’s arsenal, but awareness and prevention can drastically lower your risk. Understanding how phishing attacks operate, recognizing warning signs, and following essential security practices all play a part in staying safe online. Remember, careful thinking before clicking is your best defense. By combining education, technology, and caution, you can outsmart phishing scammers and keep your information secure in today’s digital world.